HAProxy + aria2 + Content Security Policy
2017-02-26T12:42:00Z.
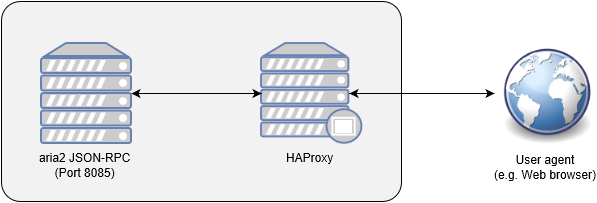
This article describes how to implement Content Security Policy (CSP) in HAProxy (acts as a reverse proxy) which is located in front of the aria2 JSON-RPC interface. All traffic between aria2 JSON-RPC interface and user agents (e.g. web browsers) pass through the HAProxy. This article assumes both aria2 and HAProxy are running on the same computer.
This article does not aim at the best CSP implementation.
HAProxy configuration
First, in the HAProxy configuration file, add the following to set CSP-related header in an HTTP response.
http-response set-header Content-Security-Policy "default-src 'self'; object-src 'none'; base-uri 'none';"
Given the above configuration, the CSP Evaluator gives some warnings about JSONP. This article does not cover how to resolve such warnings.
Next, define the aria2 JSON-RPC interface as a backend. Again, in the HAProxy configuration file, add the following:
backend backend-aria2-rpc
server server-01 127.0.0.1:8085
You may need to change the port number according to your aria2 RPC configuration.
Next, define an ACL and redirect matching traffic to the aria2 JSON-RPC interface. Again, in the HAProxy configuration file, add the following:
acl acl-aria2-rpc path_beg -i /jsonrpc
use_backend backend-aria2-rpc if acl-aria2-rpc
Reload or restart HAProxy to make the new configuration in effect.
With the above configuration, the requests sent to the aria2 JSON-RPC can
be sent like other plain old AJAX requests, and you do not need to enable
the rpc-allow-origin-all option in aria2.